Ransomware #WannaCry
The ransomware encrypts users' files and demands $300 (£230) to restore them.
Only about $50,000 (£39,000) has been paid so far, it is paid as internet currency Bitcoin.
It threatens to delete files within seven days if no payment is made.
What is Ransomware?
Ransomware is a type of malicious software that takes over the access to all computer files by encrypting it and then threatens to publish it until a ransom is paid.
What does Ransomware do?
Ransomware encrypts all the files of the infected computer and changes the affected file extension names to “.WNCRY”, so an infected file will look something like: original_name_of_file.doc.WNCRY, for example. The encrypted files are also started by the “WANACRY!” string at the beginning of the file.
Desktop will show the message like below:
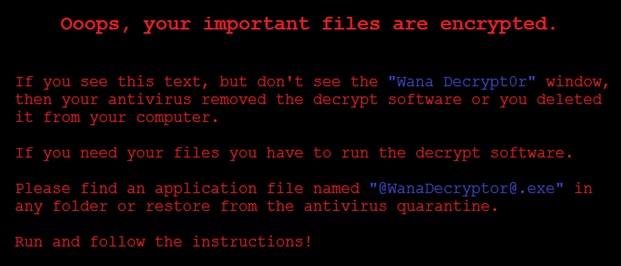
You may find their readme file saying the same message:
Ooops, your important files are encrypted.
If you see this text, but don’t see the “Wana Decrypt0r” window, then your antivirus removed the decrypt software or you deleted it from your computer.
If you need your files you have to run the decrypt software.
Please find an application file named “@WanaDecryptor@exe” in any folder or restore from the antivirus quarantine.
Run and follow the instructions!
If you run the decrypt software, or it may come automatically in your desktop saying
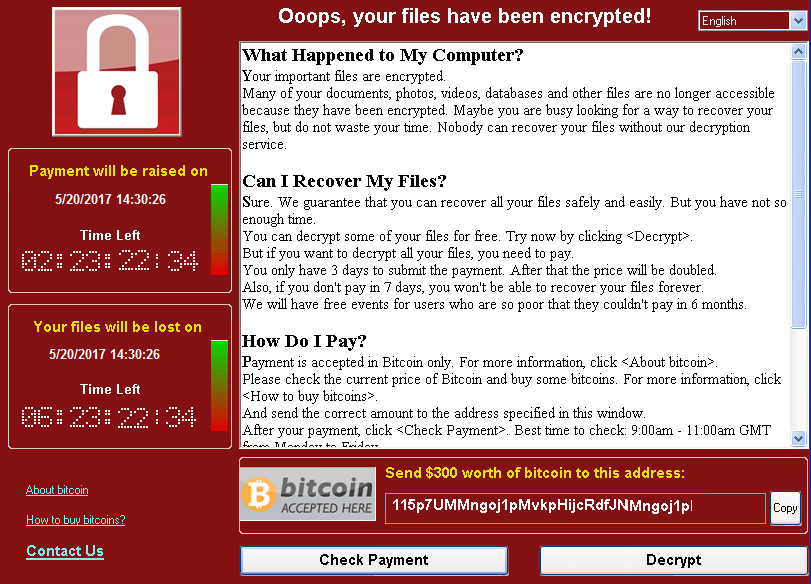
It describes:
What happened to my computer?
Your important files are encrypted.
Many of your documents, photos, videos, databases and other files are no longer accessible because they have been encrypted. Maybe you are looking for a way to recover your fines, but do not waste your time. Nobody can recover your files without our decryption service.
It also describes how you can recover your files by paying the money through bitcoin. It also threatens to increase payment amount after a certain time and to delete the files if provided time is elapsed.
Technical details of #WannaCry ransomware
WannaCrypt creates the following registry keys:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\\
= "<malware working directory>\tasksche.exe" - HKLM\SOFTWARE\WanaCrypt0r\\wd = "<malware working directory>"
It amends the wallpaper to a ransom message by modifying the following registry key:
- HKCU\Control Panel\Desktop\Wallpaper: "<malware working directory>\@WanaDecryptor@.bmp"
It creates the following files in the malware’s working directory:
- 00000000.eky
- 00000000.pky
- 00000000.res
- 274901494632976.bat
- @Please_Read_Me@.txt
- @WanaDecryptor@.bmp
- @WanaDecryptor@.exe
- b.wnry
- c.wnry
- f.wnry
- m.vbs
- msg\m_bulgarian.wnry
- msg\m_chinese (simplified).wnry
- msg\m_chinese (traditional).wnry
- msg\m_croatian.wnry
- msg\m_czech.wnry
- msg\m_danish.wnry
- msg\m_dutch.wnry
- msg\m_english.wnry
- msg\m_filipino.wnry
- msg\m_finnish.wnry
- msg\m_french.wnry
- msg\m_german.wnry
- msg\m_greek.wnry
- msg\m_indonesian.wnry
- msg\m_italian.wnry
- msg\m_japanese.wnry
- msg\m_korean.wnry
- msg\m_latvian.wnry
- msg\m_norwegian.wnry
- msg\m_polish.wnry
- msg\m_portuguese.wnry
- msg\m_romanian.wnry
- msg\m_russian.wnry
- msg\m_slovak.wnry
- msg\m_spanish.wnry
- msg\m_swedish.wnry
- msg\m_turkish.wnry
- msg\m_vietnamese.wnry
- r.wnry
- s.wnry
- t.wnry
- TaskData\Tor\libeay32.dll
- TaskData\Tor\libevent-2-0-5.dll
- TaskData\Tor\libevent_core-2-0-5.dll
- TaskData\Tor\libevent_extra-2-0-5.dll
- TaskData\Tor\libgcc_s_sjlj-1.dll
- TaskData\Tor\libssp-0.dll
- TaskData\Tor\ssleay32.dll
- TaskData\Tor\taskhsvc.exe
- TaskData\Tor\tor.exe
- TaskData\Tor\zlib1.dll
- taskdl.exe
- taskse.exe
- u.wnry
WannaCrypt may also create the following files:
- %SystemRoot%\tasksche.exe
- %SystemDrive%\intel\<random directory name>\tasksche.exe
- %ProgramData%\<random directory name>\tasksche.exe
It may create a randomly named service that has the following associated ImagePath: "cmd.exe /c "<malware working directory>\tasksche.exe"".
It then searches the whole computer for any file with any of the following file name extensions:
.123, .jpeg , .rb , .602 , .jpg , .rtf , .doc , .js , .sch , .3dm , .jsp , .sh , .3ds , .key , .sldm , .3g2 , .lay , .sldm , .3gp , .lay6 , .sldx , .7z , .ldf , .slk , .accdb , .m3u , .sln , .aes , .m4u , .snt , .ai
, .max , .sql , .ARC , .mdb , .sqlite3 , .asc , .mdf , .sqlitedb , .asf , .mid , .stc , .asm , .mkv , .std , .asp , .mml , .sti , .avi , .mov , .stw , .backup , .mp3 , .suo , .bak , .mp4 , .svg , .bat , .mpeg , .swf , .bmp , .mpg , .sxc , .brd , .msg , .sxd , .bz2 , .myd , .sxi , .c , .myi , .sxm , .cgm , .nef , .sxw , .class , .odb , .tar , .cmd , .odg , .tbk , .cpp , .odp , .tgz , .crt , .ods , .tif , .cs ,
.odt , .tiff , .csr , .onetoc2 , .txt , .csv , .ost , .uop , .db , .otg , .uot , .dbf , .otp , .vb , .dch , .ots , .vbs , .der” , .ott , .vcd , .dif , .p12 , .vdi , .dip , .PAQ , .vmdk , .djvu , .pas , .vmx , .docb ,
.pdf , .vob , .docm , .pem , .vsd , .docx , .pfx , .vsdx , .dot , .php , .wav , .dotm , .pl , .wb2 , .dotx , .png , .wk1 , .dwg , .pot , .wks , .edb , .potm , .wma , .eml , .potx , .wmv , .fla , .ppam ,
.xlc , .flv , .pps , .xlm , .frm , .ppsm , .xls , .gif , .ppsx , .xlsb , .gpg , .ppt , .xlsm , .gz , .pptm , .xlsx , .h , .pptx , .xlt , .hwp , .ps1 , .xltm , .ibd , .psd , .xltx , .iso , .pst , .xlw , .jar , .rar ,
.zip , .java , .raw.
WannaCrypt encrypts all files it finds and renames them by appending .WNCRY to the file name.
This ransomware also creates the file @Please_Read_Me@.txt in every folder where files are encrypted.
Spreading capability
Ransomware attempts to infect unpatched Windows machines in the local network. It also scans internet as well as intranet IP addresses to find and infect other vulnerable computers. It generates large amount of SMB traffic [port 445] from the infected host.
How can it be prevented?
Microsoft has already released security fix for preventing this malware. But the windows machines which are not up-to-date, is vulnerable.
Update the security patch in all the Windows machines or if your operating system is outdated, upgrade to Windows 10.
Microsoft has recommended to customers who have not yet installed the security update MS17-010 do so as soon as possible. Until you can apply the patch, add a rule on the router or firewall to block incoming SMB traffic on port 445
- 55 reads